Topic: Install Full disk encryption (including /boot ) Luks2+argon2id T440P
Hi all.
I would like to share my experience of installing Hyperbola with Libreboot+Luks2+argon2id with an encrypted boot partition.
This is a test setup. There are still questions left:
1. Password for Grub https://libreboot.org/docs/linux/grub_h … t-with-gpg
2. If you insert a second SSD, how to configure Grub so that it is also encrypted.
3. Change the picture, I would put the Hyperbola screensaver if there is a beautiful photo https://github.com/vinceliuice/grub2-themes
A short preface.
Unfortunately, there is very little documentation on this installation, what I found on the Internet were options
installations without an encrypted boot partition or option with Luks1. Sometimes it seemed to me as if the information was deliberately hidden from the user)) I also looked for answers in reddit, but very often I came across answers like this https://teddit.zaggy.nl/r/coreboot/comm … ncryption/ or https //teddit.zaggy.nl/r/coreboot/comments/1903q0o/grub2_as_coreboot_payload/ that is, 95% of users do not receive answers to questions on this topic.
On the Libreboot website there is a section dedicated to "Encrypted /boot via LUKS2 with argon2" https://libreboot.org/docs/linux/#encry … ith-argon2 which, in my opinion, provides general information, but this is not similar to the instructions or Arch wiki or how it was done in Parabola https://wiki.parabola.nu/Installing_Par … e_the_ROM.
I wanted to say thank you to Throgh who helped me and answered my questions, which helped me. Wael from Parabola also helped me answer questions. The user Cat also helped me. Coreboot and Libreboot did not help me on the IRC channel!
My test was carried out on a T440P computer. If the GRUB in the ROM supports LUKS2, then it can unlock the drive and boot the distribution directly - you don't even have to install GRUB in your distribution. GRUB is already part of libreboot and is flashed together
with it as payload
There is code in GRUB that can be used to unlock LUKS1 and LUKS2 dm-crypt using the cryptomount command.
Thanks to this, you can boot with full disk encryption by encrypting /boot.
Libreboot’s argon2 patches are based on this AUR repository https://aur.archlinux.org/cgit/aur.git/ … 9fa4c2f50d which patched GRUB 2.06, and the patches were rebased for use with GRUB 2.12 which Libreboot uses; the rebase was performed by Nicholas Johnson https://libreboot.org/news/argon2.html#introduction
This assumes you are doing a fresh installation, I followed my instructions but used:
--pbkdf argon2id
--type luks2
# cryptsetup -v --cipher aes-xts-plain64 --hash sha512 --iter-time 10000 --key-size 512 --pbkdf argon2id --use-urandom --verify-passphrase luksFormat --type luks2 /dev/sda1This computer requires the implementation of blob-objects, if you do not do this it will not work.
In order for Luks2 to work with argon2id, it is recommended to download the latest versions of Libreboot 20231106 or 20240126 https://mirrors.mit.edu/libreboot/testi … 1106/roms/ (argon2/luks2 has been supported since August)
I used 20231106 in the test. You need to download libreboot-20231106_t440pmrc_12mb.tar.xz to check the authenticity of the file, then unpack and select the version grub_t440pmrc_12mb_libgfxinit_corebootfb_usqwerty.rom or select your language, at the end of the file you will see deqwertz.rom de German etc.
Next, you need to embed blobs into ROM; this is a peculiar procedure that requires about 8GB of free disk space and about an hour of time (this was the case for me)
Written in detail here https://libreboot.org/docs/install/t440p_external.html. You don't need to disassemble your computer, you embed the blobs and then use the flashrom utility.
Install flashrom
$ doas pacman -S flashromBefore updating the release, you need to boot into Linux with the kernel parameter "iomem=relaxed". The Linux kernel, starting with version 4.4, blocks access to the ROM as a security measure, so when starting the flashrom, an error like “/dev/mem mmap error” will be displayed. To get around this, you need to tell the kernel to allow access to low-level hardware for boot time.
Once you get to the grub menu, you can edit the default menu entry by pressing "e". Use your arrow keys to navigate to the line starting with "linux" and add "iomem=relaxed" to the end of the line. After editing, press Ctrl +x
or
Turn on your computer and, depending on the version of SeaBios (press "Esc" then "c") or Grub (press "c"), enter:
cryptomount -a
set root='lvm/matrix-rootvol'
linux /boot/vmlinuz-linux-libre root=/dev/matrix/rootvol cryptdevice=/dev/sda1:lvm iomem=relaxed
initrd /boot/initramfs-linux-libre.img
bootAfter the computer has booted, let's check by entering in the terminal:
$ cat /proc/cmdlineyou should see at the end iomem=relaxed
BOOT_IMAGE=/boot/vmlinuz-linux-libre root=/dev/matrix/rootvol cryptdevice=/dev/sda1:lvm iomem=relaxedYour computer is now ready.
Next you need to edit Libreboot's grub.cfg and add these lines:
.......
echo #Insert newline
}
menuentry 'Load Hyperbola GNU/Linux-Libre (LTS)' {
insmod ahci
insmod part_msdos
insmod lvm
insmod cryptodisk
cryptomount -a
set root='lvm/matrix-rootvol'
linux /boot/vmlinuz-linux-libre root=/dev/matrix/rootvol cryptdevice=/dev/sda1:lvm
initrd /boot/initramfs-linux-libre.img
}
menuentry 'Search ISOLINUX menu (AHCI) [a]' --hotkey='a' {
......Remove this part of the code since I'm not using raid:
menuentry 'Load Operating System (incl. fully encrypted disks) [o]' --hotkey='o' {
if [ "${grub_scan_disk}" != "ata" ]; then
search_grub ahci
fi
if [ "${grub_scan_disk}" != "ahci" ]; then
search_grub ata
fi
# grub device enumeration is very slow, so checks are hardcoded
# TODO: add more strings, based on what distros set up when
# the user select auto-partitioning on those installers
lvmvol="lvm/matrix-bootvol lvm/matrix-rootvol"
raidvol="md/0 md/1 md/2 md/3 md/4 md/5 md/6 md/7 md/8 md/9"
# in practise, doing multiple redundant checks is perfectly fast and
# TODO: optimize grub itself, and use */? here for everything
for vol in ${lvmvol} ${raidvol} ; do
try_user_config "${vol}"
done
unset ahcidev
unset atadev
for i in 11 10 9 8 7 6 5 4 3 2 1 0; do
for part in 20 19 18 17 16 15 14 13 12 11 10 9 8 7 6 5 4 3 2 1; do
if [ "${grub_scan_disk}" != "ata" ]; then
ahcidev="(ahci${i},${part}) ${ahcidev}"
fi
if [ "${grub_scan_disk}" != "ahci" ]; then
atadev="(ata${i},${part}) ${atadev}"
fi
done
done
set pager=0
echo -n "Attempting to unlock encrypted volumes"
for dev in ${ahcidev} ${atadev} ${lvmvol} ${raidvol}; do
if cryptomount "${dev}" ; then break ; fi
done
set pager=1
echo
# after cryptomount, lvm volumes might be available
for vol in ${lvmvol}; do
try_user_config "${vol}"
done
search_grub crypto
if [ "${grub_scan_disk}" != "ata" ]; then
# Last resort, if all else fails
set root=ahci0,1
for p in / /boot/; do
if [ -f "${p}vmlinuz" ]; then
linux ${p}vmlinuz root=/dev/sda1 rw
if [ -f "${p}initrd.img" ]; then
initrd ${p}initrd.img
fi
fi
done
fi
if [ "${grub_scan_disk}" != "ahci" ]; then
# Last resort (for setups that use IDE instead of SATA)
set root=ata0,1
for p in / /boot/; do
if [ -f "${p}vmlinuz" ]; then
linux ${p}vmlinuz root=/dev/sda1 rw
if [ -f "${p}initrd.img" ]; then
initrd ${p}initrd.img
fi
fi
done
fi
true # Prevent pager requiring to accept each line instead of whole screenSaves changes.
To add, change or remove grub.cfg you need the "cbfstool" utility
You can download the utility like this:
wget https://mrchromebox.tech/files/util/cbfstool.tar.gz && tar -zxf cbfstool.tar.gzLet's check the Libreboot ROM with the command:
./cbfstool let to your ROM print
./cbfstool /home/jim/Downloads/grub_t440pmrc_12mb_libgfxinit_corebootfb_usqwerty.rom ptintYou will find that there is no grub.cfg in the Libreboot ROM because https://libreboot.org/docs/linux/grub_c … t-grub.cfg has changed.
FMAP REGION: COREBOOT
Name Offset Type Size Comp
cbfs_master_header 0x0 cbfs header 32 none
fallback/romstage 0x80 stage 45464 none
cpu_microcode_blob.bin 0xb2c0 microcode 63488 none
intel_fit 0x1ab00 (unknown) 112 none
fallback/ramstage 0x1abc0 stage 115811 LZMA (241176 decompressed)
config 0x37080 raw 3008 LZMA (9738 decompressed)
revision 0x37c80 raw 705 none
build_info 0x37f80 raw 90 none
fallback/dsdt.aml 0x38000 raw 14002 none
vbt.bin 0x3b700 raw 1410 LZMA (4608 decompressed)
cmos.default 0x3bcc0 cmos_default 256 none
cmos_layout.bin 0x3be00 cmos_layout 1296 none
fallback/postcar 0x3c340 stage 20940 none
img/memtest 0x41580 simple elf 58104 none
seabios.elf 0x4f8c0 simple elf 64092 none
etc/ps2-keyboard-spinup 0x5f340 raw 8 none
etc/pci-optionrom-exec 0x5f380 raw 8 none
etc/optionroms-checksum 0x5f3c0 raw 8 none
vgaroms/seavgabios.bin 0x5f400 raw 26112 none
fallback/payload 0x65a40 simple elf 533608 none
background.png 0xe7f00 raw 3451 none
scan.cfg 0xe8cc0 raw 26 none
keymap.cfg 0xe8d00 raw 16 none
(empty) 0xe8d40 null 7352100 none
bootblock 0x7ebc80 bootblock 16704 noneNow, before using the updated grub.cfg, let's check how it works using grubtest.cfg. It is very important!
grubtest.cfg contains the same information as grub.cfg .
Add grubtest.cfg to your ROM with the command:
./cbfstool /home/jim/Downloads/grub_t440pmrc_12mb_libgfxinit_corebootfb_usqwerty.rom add -n grubtest.cfg -f /home/jim/grubtest.cfg -t rawTo remove grubtest.cfg or grub.cfg use the command:
./cbfstool /home/jim/Downloads/grub_t440pmrc_12mb_libgfxinit_corebootfb_usqwerty.rom remove -n grubtest.cfgExtract grub.cfg
./cbfstool /home/jim/Downloads/grub_t440pmrc_12mb_libgfxinit_corebootfb_usqwerty.rom extract -n grub.cfg -f grub.cfgNow check again, you should see grubtest.cfg at the very bottom of the list
./cbfstool /home/jim/Downloads/grub_t440pmrc_12mb_libgfxinit_corebootfb_usqwerty.rom ptintNow we need to update our ROM. Since our computer is already ready for this trick) Execute:
$ doas flashrom -p internalThere are no errors, ok, now let’s execute:
$ doas flashrom -p internal -w grub_t440pmrc_12mb_libgfxinit_corebootfb_usqwerty.rom...and wait for the message “Verifying flash... VERIFIED.”. Once you do this, turn off your computer and boot into the new configuration.
The boot process may ask for the passphrase twice: first GRUB asks for it, and then the init system asks for it again because GRUB cannot pass the passphrase or the unlock state to the init system.
in the Grub menu you will see:
*Load test configuration (grubtest.cfg) inside of CBFS(t)
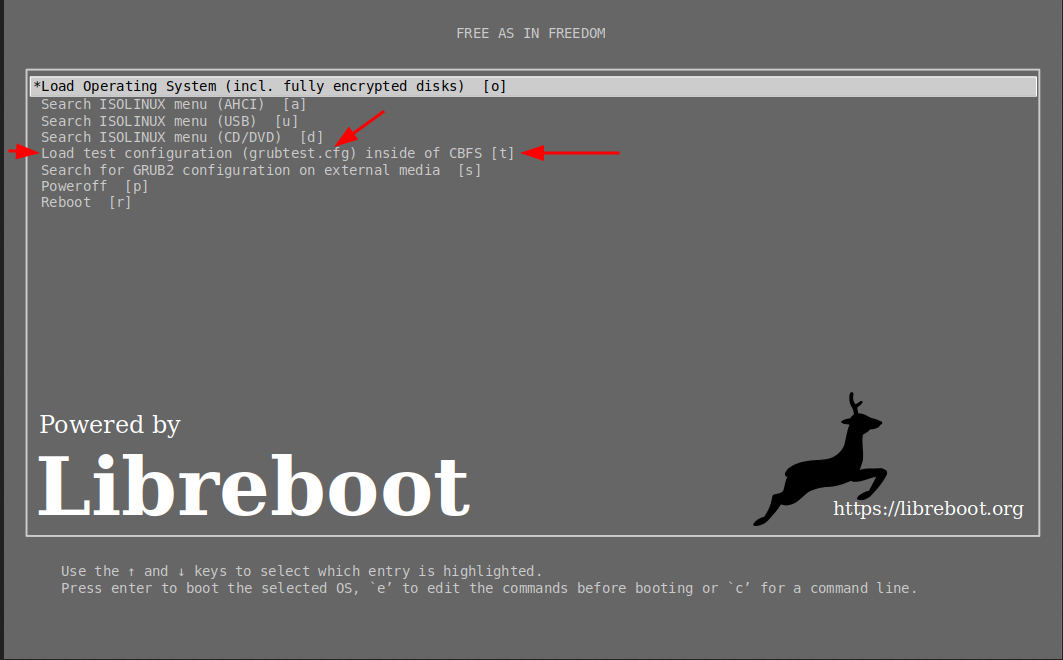
Select and press "Enter"
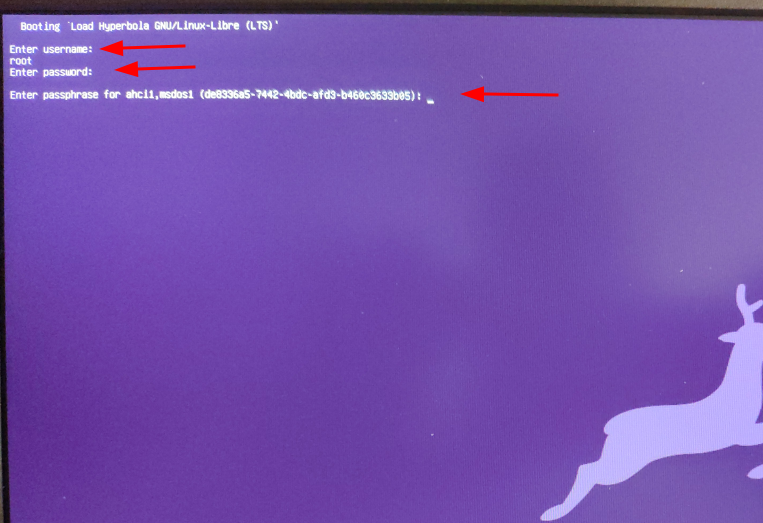
You will be greeted by the following message that will ask you to enter a password.
Enter passphrase for ahci1,msdos (9283749-23423429-2893749823-23894):
Next, you need to enter the password for your encrypted disk again.
Enter passphrase for /dev/sda1
If everything went well, change grubtest.cfg to grub.cfg and try this trick again. Just rename the file.
You can also change grub.cfg so that after booting the computer you do not have the Grub menu.
set timeout=10
on
set timeout=0and after booting the computer, instead of the Grub menu you will see the following message:
Enter passphrase for ahci1,msdos (9283749-23423429-2893749823-23894):
At the moment everything is working well, but after entering the password I get the message:
error: AHCI transfer error but even with this error everything works stably.
When I deleted the DVD there was no more error)) And I liked it so much, it’s old school))
If you have anything to add, please write...